According to Gartner Inc., by 2023, 65% of the world’s population will have its data covered under modern privacy regulations. In the U.S., the number of data breaches specifically has skyrocketed and grown from a data breach of 471 million sensitive records in 2018 to 156 million records in 2020. And the highest contributing factor behind this breach was security system complexity and cloud migration, as figured out in reports by Statista. Whatever be the enterprises’ digital Achilles’ heel, such incidents of a data breach are demanding sound cybersecurity practices and security controls.
There needs to be business enablement for data privacy and security by leaders. Just because these business complexities exist organizations must not simplify and streamline their operations thoughtlessly, but consciously and deliberately. Not just technological implementation but leaders must focus on these questions that tend to get short shrifts, but can yield significant dividends:
- Instilling a culture of cybersecurity
- Cyber risk management
- Communication between management and board
- Aligning cyber with overall business goals
Tech in itself is not a satisfactory solution to simplified cybersecurity, it must be a concern for the entire business for data privacy in every function and every employee. Let’s check how business enablement would work for data privacy.
What Business Enablement’s Would Better Manage Cyber Risks?
Data privacy enablement should be positioned to address, enable, enhance, and preserve the entire lifecycle of data and also let businesses smoothly pursue data sharing and collaboration practices, overcoming the regulatory barriers as well. Here are some business enablements for data privacy that must be taken care of:
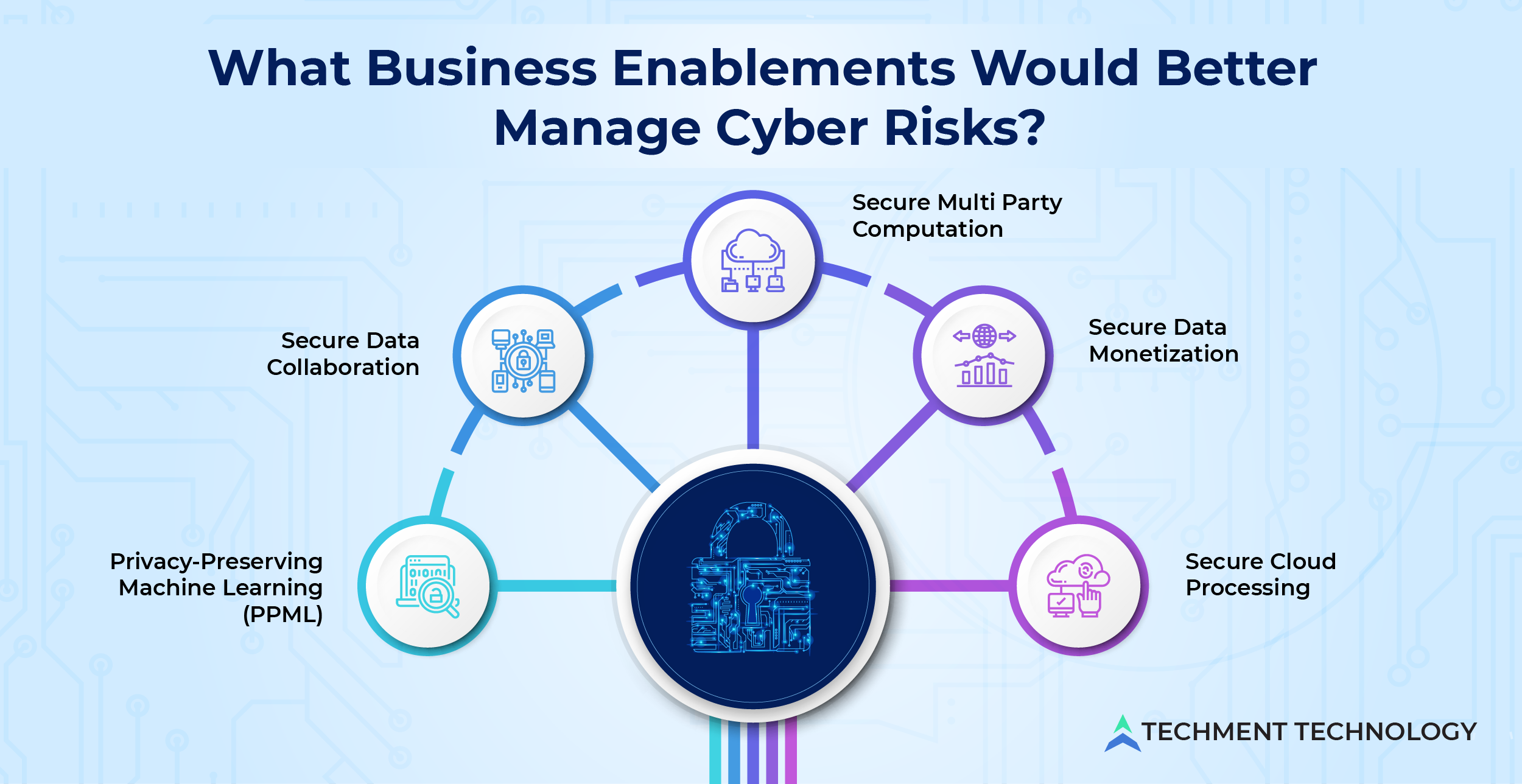
- Secure Data Collaboration: Augmenting data and insights with partners or consultants can make decisions smarter but before data collaboration having specific KPIs will ensure secure opportunities in the future. Partnerships and alliances for data are now sought because without disclosing the raw data companies can help each other with macroeconomic insights. Using a data cloud enables organizations to share governed data without copying or moving it. This makes possible data accessibility with data modeling and BI tools.Creating a “clean room” is a much-protected way of secure data collaboration. It is a secure environment with a de-identified and aggregated data set, enabling the connection of distributed data across multiple platforms and parties. It is meant to protect private and proprietary data through obfuscation.
- Privacy-Preserving Machine Learning (PPML): The data science industry realizes the breadth of roles of machine learning. Companies that are adapting multiple products and services across different geographies are unlocking hyper-local AI/ ML, this brings substantial business benefits and improved customer engagement. The current cloud computing adoption scenario for machine learning (ML) questions the security of data which gave rise to the Privacy-Preserving Machine Learning approach (PPML). This technique implies various methods like differential privacy, homomorphic encryption, and decentralized ML processes are some that prevent the privacy information from being exposed.
- Secure Data Monetization: When data is processed for economic benefits either by internal (indirect) method for business performances or by external (direct) methods i.e., data sharing to gain beneficial terms from partners or brokers are called data monetization. According to research by Data Bridge Market Research, the data monetization market is expected to witness market growth at a rate of 21.95% in the forecast period of 2022 to 2029. For secure data monetization emphasizing solid privacy and security strategy must be foundational through a data-centric model. For the B2B market bringing a data-centric security strategy is more appealing to partners, suppliers, and collaborators.
- Secure Cloud Processing: Cloud migration and adoption intensify the strong endpoint security like anti-malware, intrusion detection, etc. For these automation tools, security capabilities with continuous monitoring should be provided with the help of protection platform tools. Requirements such as patch management, endpoint encryption, VPNs, and others are addressed by security tools required for cloud processing.
- Secure Multi Party Computation: This method helps businesses ensure the security of their sensitive data without undermining their ability to gain insights from it. This cryptographic technique enables different parties to carry out computation using their private data without revealing them to each other. The secure multi-party computation eliminates the tradeoff between data privacy and data utility and eliminates the risk of data breaches and misuses stemming from data collection.
According to research done by PwC on 3602 respondents, “2022 Global Digital Trust Insights, October 2021”, 42% of respondents confirmed that their organization made progress in the past two years when they increased the alignment of cybersecurity strategy to business strategy, and 46% responded in favor of increased engagement when CEOs were directly involved in cyber security matters.
In a complex business environment, organizational complexity is posing concerns of cybersecurity and privacy risk, because of which enterprises must simplify their operations and processes consciously and deliberately.
Conclusion:
Checking on Digital Supply Chain will Reconceptualize Data Privacy
Investment continues to pour into cybersecurity as organizations know that risks are increasing. As our digital systems are growing more complex, the consequences of attacks become more severe. Companies must create and adhere to the processes for dealing with data and third-party risk management. C-suit champions must develop new habits of collaboration among all businesses, functions, and tech for an organization that’s simply secure.
In 2022, the digital supply chain (a set of processes that involve advanced technologies and better insights into the function of each stakeholder) is more vulnerable to attacks by cybercriminals. This is demanding new mitigation approaches that involve more deliberate risk-based vendor segmentation and scoring, security controls, and best practices to bring a shift in resilient-based efforts to get ahead in security regulations.
Security compliances must be reconceptualized and focus on the gaps where needed, for data privacy. Techment Technology focuses on building data privacy and protection strategy and implementing appropriate safeguards while venturing into data science and engineering. For getting detailed insights on data handling procedures get our free consultation.
 All Posts
All Posts