Single Cyber Attack Fretting the Sensitive Enterprise Data
The overwhelming digital innovation in recent years has broadened the practices that IT companies are following especially in applications development. Given customer retention and boosting customer relationships, they put customer convenience at the heart of development and sometimes miss the security practices. The most common assumption related to application development security is that it starts from the initial phase of development which is true but the other side of it is “it never stops”.
Rising Threat and is Cost
In a recent incident computer giant, Acer was hit by a ransomware attack in March 2021 and demanded $ 50 million which is the largest known ransom in a security attack to date. The gang revealed the leak of financial spreadsheets, bank balances, and communications. The ransomware attack have grown which claims a new victim every 5 seconds in 2021, according to Cybersecurity Ventures (world’s leading researcher in global cyber economy); also the damage cost due to this is expected to reach $ 20 billion by the end of 2021 which is 57 times more than it was in 2015. So the companies must foresee what security measure would safeguard their future practices of development without compromising the customer experience.
With the rise in blockchain, cryptocurrency users saw cryptojacking, a new cyberattack activity where criminals hijack third-party home or work computers to “mine” cryptocurrency; proving that even the strongest security measures like crypto hash algorithm-1 (SHA-1) can be intervened by attackers. So consistent security practices are a must.
What are the Best Security Practices for Companies?
In recent years there has been a rise in security threats and developers need to be more aware of the status of application security. They need to take both the development process and security measures hand-in-hand. So following practices must be included:
- Regular Testing: To avoid frequent attack threats, developers must do regular testing. After an attack has been done and then adopting measures can heavily hit the company in terms of economy as well as data. So implying emulators, threat modeling or penetration testing (pen testing) are some security measures at the initial stage.
- Secure Codes: When it comes to cyber-attack, both companies and developers must choose secure codes as attackers find it easy to attack when the code is weak or it’s a public code. To prevent break-ins they must write their code and enhance the toughness level in codes.
But the level of attacks and the vulnerable areas of attack can vary in application development and unawareness about the same can make them heavily prone to attacks. Before practicing any security measures developers and testers should be aware of what threats they can get.
Enterprises Need to be Aware of These Attacks & Their Preventions
Avoiding enough precautionary measures can make companies compromise their application security. By becoming aware at each level of the development process they can avoid security threats and potentially lessen the damage that could be caused.
- SQL Injections: When attackers make changes to queries that an application makes to its database then an SQL injection has been made. They modify or delete data that causes a persistent change in application. The best practice to prevent such an attack is to perform penetration testing, which tests the vulnerabilities in infrastructure i.e., in OS, improper configurations, or end-user behavior. Commercial vulnerability scanners or source code analyzers are other options. They may not necessarily uncover all vulnerabilities, so using multiple scanners would be the best practice.
- Cross-Site Scripting: One of the popular vulnerabilities is cross-site scripting or XSS that injects malicious codes into running applications and can affect the client-side by affecting their device with malware and stealing sensitive information. Implementing CSP (Content Security Policy) should be in the policy of security measures which adds a layer of protection against XSS and other code injection attacks.
- Zero Delay Exploits: When the hacker attacks before the developer can address it, it’s a Zero delay attack. They usually target OS, office applications, web browsers, open-source components, hardware, and firmware. Zoom, a popular video conferencing platform was the victim of this attack in 2020, where attackers attacked older versions of Windows and OS. The best choice to avoid such an attack is to keep the software and OS updated.
Of course, security vulnerabilities cannot be completely avoided in the system and development process; however, the state of network and infrastructure security can be significantly improved by reducing the severity of vulnerabilities that are created. The most important approach is to follow the principles of secure application and software development and to ensure that developers have sufficient security expertise.
5 Cyber Security Trends to Secure Infrastructure and System
To fend off the cyber intrusion attempts, organizations must find ways to use security solutions in their security operations, threat analysis and provide a faster and more effective response to a wide range of threats with minimal human intervention.
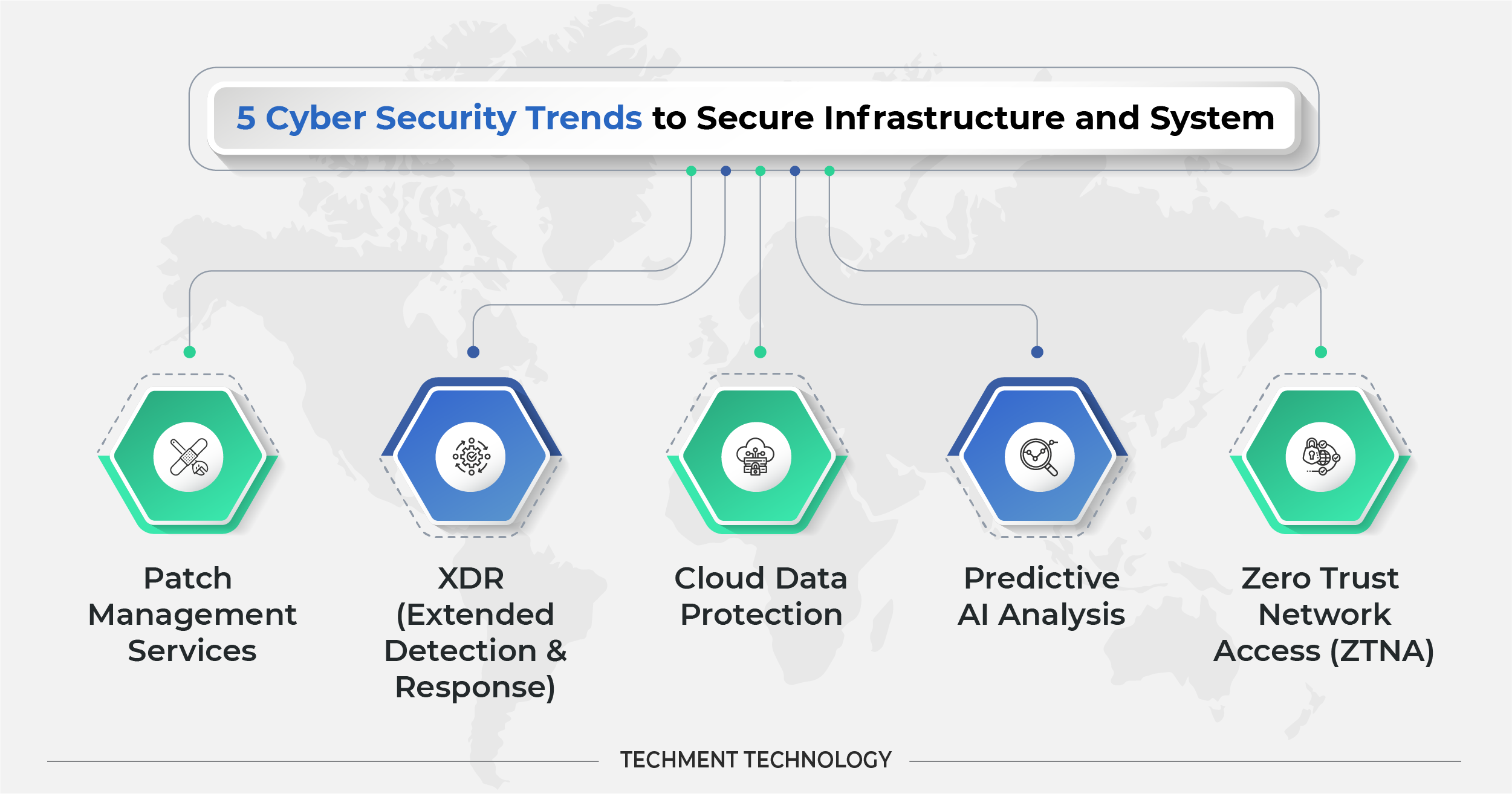
- Patch Management Services: Using outdated legacy systems weakens the security of the system as older software sometimes can not be managed to test the vulnerabilities. Unpatched weaknesses in the computer system are primary infiltration points for criminals. So patch management needs to be done to remove bugs. Patches are the code fixes that test the attack vulnerabilities, and patch management is the process of identifying, prioritizing, remediating, and reporting issues in OS and software. Earlier the internal IT team was responsible for patch management but now they choose to outsource it to SaaS providers, without having to install 3rd party tools, as teams struggle to keep up the patches in larger organizations.
- XDR (Extended Detection & Response): XDR is the cybersecurity tool that monitors and mitigates cyber threats. XDR is mainly a SaaS-based, vendor-specific, security threat detection and incident response tool that natively integrates multiple security products into a cohesive security operating system that unifies all licensed components. Applying analytics and automation, it delivers data across networks, clouds and endpoints. Since it is vendor-based, it lowers the cost of ownership for effective detection.
Microsoft 365 Defender, provides XDR for small-medium-sized businesses for Windows. It depends heavily on AI to check security issues and self-healing capabilities for automation. Azure Defender, delivers XDR capabilities to protect a multi-cloud, hybrid-cloud workload, including virtual machines, databases, containers, IoT, and more.
- Cloud Data Protection: The work-from-home scenario has largely created a need for data protection for employees who rely on cloud services like Zoom and Slack. The organizations relying on the cloud are more prone to data breaches, leaks, insecure APIs, misconfigured storage, etc. Access control, encryption, secure deletion, and data masking are all data protection methods in the cloud. Different cloud providers provide security differently. Some rely on AI tools to protect data and auto-patching. IBM Cloud Security by IBM is one of the most recognized data security portfolio vendors and it is highly recognized because of its market approach, innovation roadmap, partner ecosystem, and data intelligence.
- Predictive AI Analysis: AI has become a critical technology in cyber security. AI can quickly detect and analyze millions of events & different types of threats from malware identification to identifying phishing attacks or download of malicious codes. The predictive behavior of AI can tell how and where you are most likely to be breached so companies can plan for resource and tool allocation towards areas of weakness.
Google Chronicle, a cloud service built by Google designed for enterprises to retain, and analyze the data to provide instant analysis and context on risky activities. The high speed at which Chronicle executes security analytics means teams can upload their security telemetry onto the platform and start analyzing it within seconds. - Zero Trust Network Access (ZTNA): Companies are now more inclined towards zero-trust network access (ZTNA) which is observed as a more secure option for controlling remote access to servers and soon will phase out VPN. ZTNA service makes applications non-discoverable, reduces the total attack surface of the network, and severely limits server to server threats with the use of micro-segmentation.
A micro-segmentation solution that makes it easy to isolate modern data centers from the environment; instead of using IP addresses and VLAN membership, it segments the network by labeling application or workload storage resources, making environment separation suitable for dynamic application environments. Micro-segmentation offers the benefits of reusable server roles, application and environment tags, reusable security policy templates, separation of platform diagnostics, automated test pipelines, and more.
As the IT environment in organizations becomes more complex, it is important for data security teams to select the right processes and tools to defend against potential cyber threats. It is imperative to have backups of important data on portable hard drives. With the rise in cybercrimes worldwide, vendors/suppliers / third parties should also be instructed to regularly check their network for possible vulnerabilities and security threats.
Making Certain the Cyber Espionage aren’t Threatening Your Future
Gone are the days when installing firewalls for network security was enough. Along with the developmental process, technology has also transformed security operations with a growing number of innovative products and services.
The new approach to troubleshooting and ensuring the uninterrupted end-user experience is securing data since the highly vulnerable factor these days is “Data” which has become a highly valuable commodity for hackers. The threats can be serious for businesses and consumers when there’s slight ignorance in adopting security practices and businesses that suffer a cyber breach will also generally incur costs associated with repairing affected systems, networks, and devices. Organizations should consider things like data privacy, record retention and destruction, encryption in transit, and network segmentation to assess where they can strengthen their data privacy. With a more realistic understanding of the potential impact of a cyberattack, leaders can invest in risk management to be safer, more vigilant, and resilient.
Practices for protecting against cyber threats must also include basic but important countermeasures such as system patches. When a technology vendor discovers (or receives notification) of a security threat in their product, they usually write code to fix the problem. Companies must adopt a proactive approach to security to ensure that all of these threats can be present and must focus more on protecting data, and align efforts to identify and protect the data assets that are most valuable to the business at the moment.
 All Posts
All Posts